RedHat EX447 Exam Questions
Questions for the EX447 were updated on : Apr 22 ,2025
Page 1 out of 2. Viewing questions 1-15 out of 26
Question 1
Install and configure ansible
User bob has been created on your control node. Give him the appropriate permissions on the
control node. Install the necessary packages to run ansible on the control node.
Create a configuration file /home/bob/ansible/ansible.cfg to meet the following requirements:
The roles path should include /home/bob/ansible/roles, as well as any other path that may be
required for the course of the sample exam.
The inventory file path is /home/bob/ansible/inventory.
Ansible should be able to manage 10 hosts at a single time.
Ansible should connect to all managed nodes using the bob user.
Create an inventory file for the following five nodes:
nodel.example.com
node2.example.com
node3.example.com
node4.example.com
node5.example.com
Configure these nodes to be in an inventory file where node1 is a member of group dev. nodc2 is a
member of group test, nodc3 is a member of group proxy, nodc4 and node 5 are members of group
prod. Also, prod is a member of group webservers.
Answer:
A
A. Explanation:
In/home/sandy/ansible/ansible.cfg
[defaults]
inventory=/home/sandy/ansible/inventory
roles_path=/home/sandy/ansible/roles
remote_user= sandy
host_key_checking=false
[privilegeescalation]
become=true
become_user=root
become_method=sudo
become_ask_pass=false
In /home/sandy/ansible/inventory
[dev]
node 1 .
example.com
[test]
node2.example.com
[proxy]
node3 .
example.com
[prod]
node4.example.com
node5 .
example.com
[webservers:children]
prod
Question 2
Create a file called adhoc.sh in /home/sandy/ansible which will use adhoc commands to set up a
new repository. The name of the repo will be 'EPEL' the description 'RHEL8' the baseurl is
'https://dl.fedoraproject.org/pub/epel/epel
-
release-latest-8.noarch.rmp'
there is no gpgcheck, but
you should enable the repo.
* You should be able to use an bash script using adhoc commands to enable repos. Depending on
your lab setup, you may need to make this repo "state=absent" after you pass this task.
Answer:
A
A. Explanation:
chmod 0777 adhoc.sh
vim adhoc.sh
#I/bin/bash
ansible all -m yum_repository -a 'name=EPEL description=RHEL8
baseurl=
https://dl.fedoraproject.org/pub/epel/epel-release-latest-8.noarch.rmp
gpgcheck=no enabled=yes'
Question 3
Create a file called packages.yml in /home/sandy/ansible to install some packages for the following
hosts. On dev, prod and webservers install packages httpd, mod_ssl, and mariadb. On dev only install
the development tools package. Also, on dev host update all the packages to the latest.
Answer:
A
A. Explanation:
Solution as: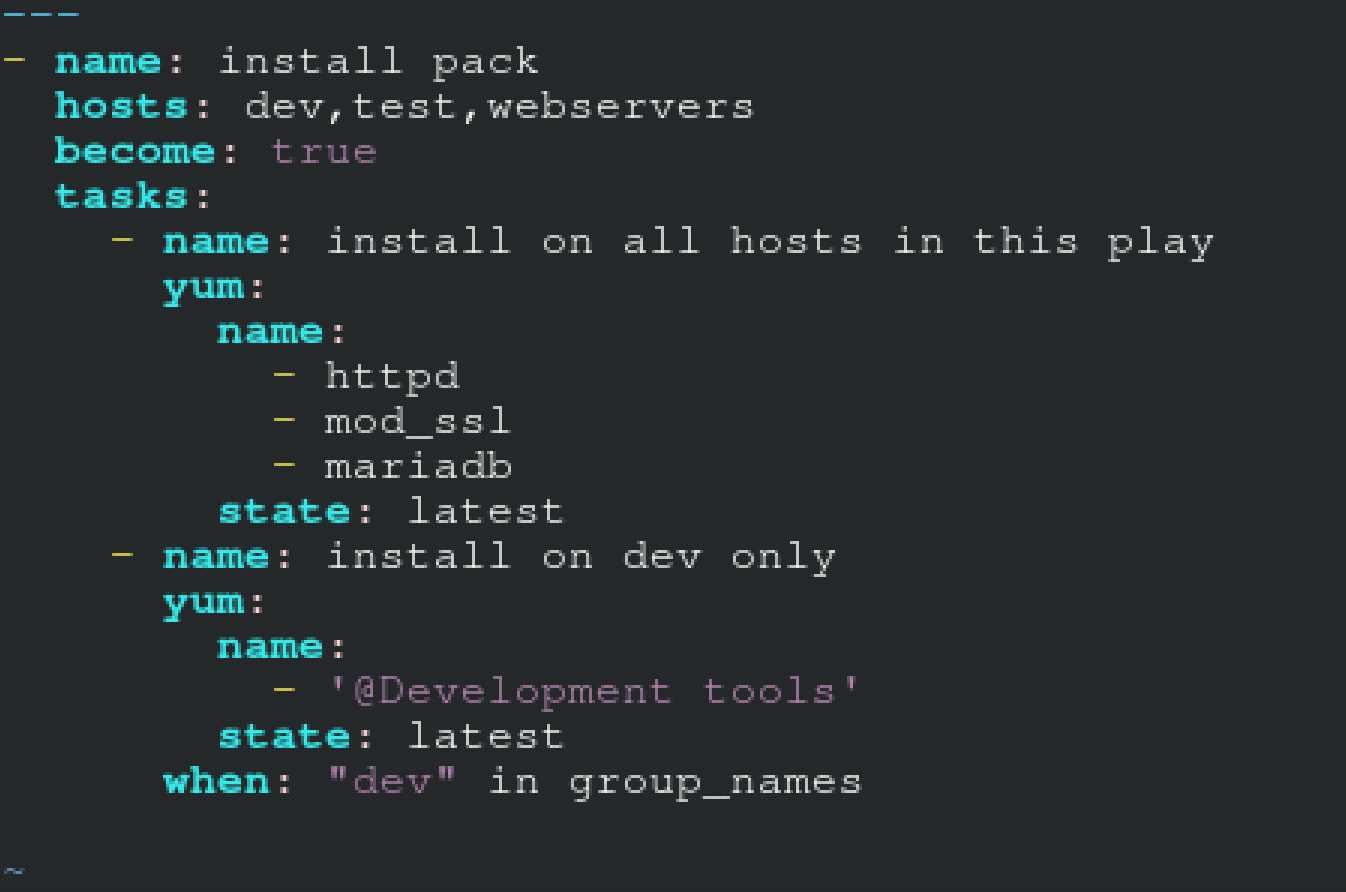
** NOTE 1 a more acceptable answer is likely 'present' since it's not asking to install the latest
state: present
** NOTE 2 need to update the development node
- name: update all packages on development node
yum:
name: '*'
state: latest
Question 4
Create a role called sample-apache in /home/sandy/ansible/roles that enables and starts httpd,
enables and starts the firewall and allows the webserver service. Create a template called
index.html.j2 which creates and serves a message from /var/www/html/index.html Whenever the
content of the file changes, restart the webserver service.
Welcome to [FQDN] on [IP]
Replace the FQDN with the fully qualified domain name and IP with the ip address of the node using
ansible facts. Lastly, create a playbook in /home/sandy/ansible/ called apache.yml and use the role
to serve the index file on webserver hosts.
Answer:
A
A. Explanation:
/home/sandy/ansible/apache.yml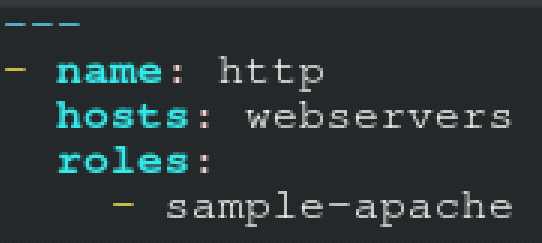
/home/sandy/ansible/roles/sample-apache/tasks/main.yml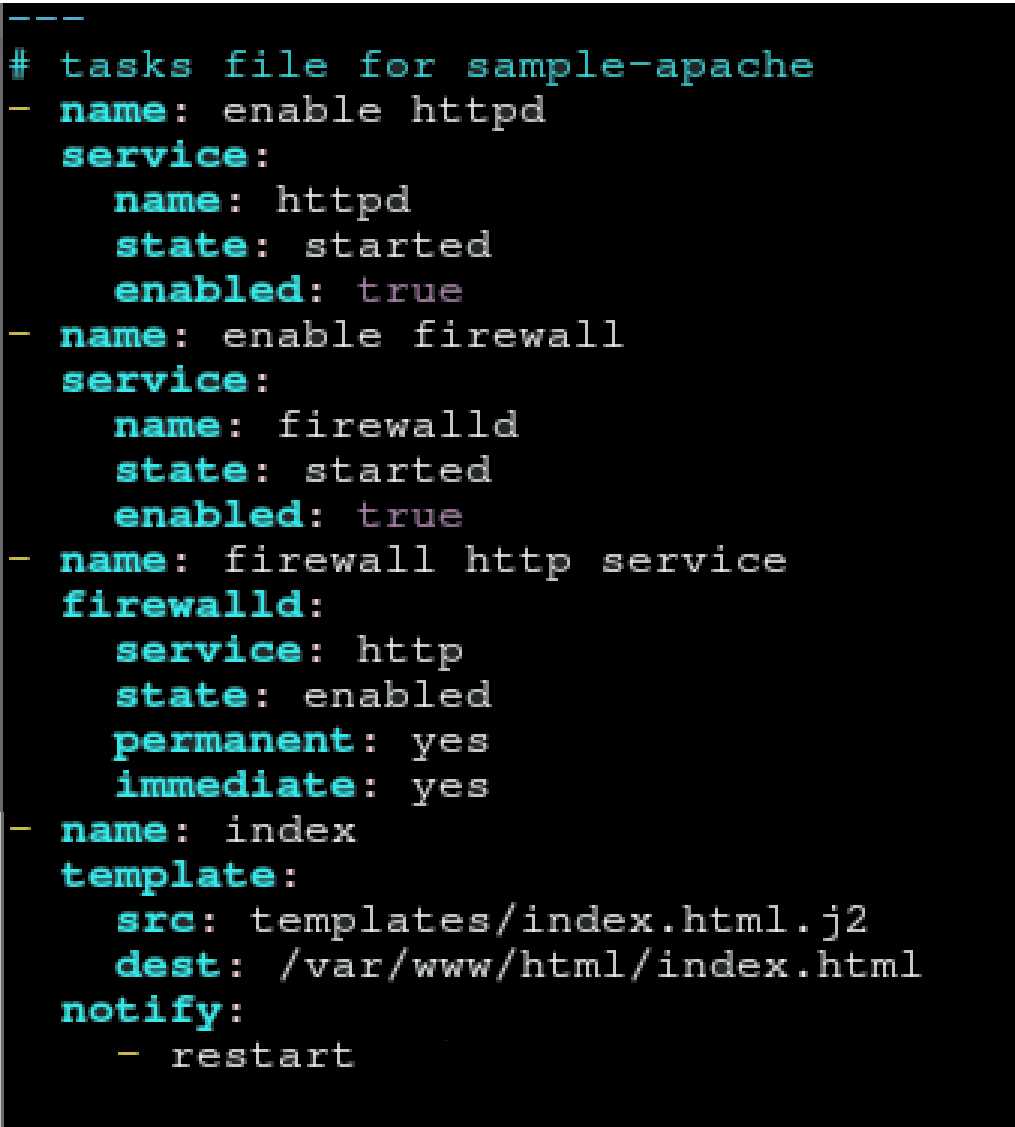 /home/sandy/ansible/roles/sample-apache/templates/index.html.j2
/home/sandy/ansible/roles/sample-apache/templates/index.html.j2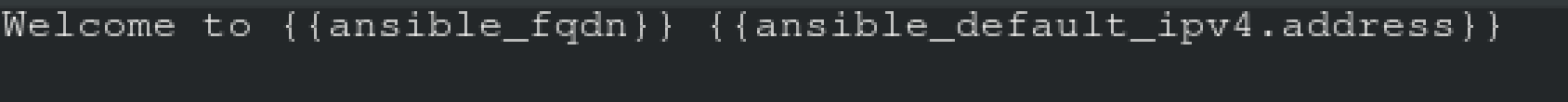
In /home/sandy/ansible/roles/sample-apache/handlers/main.yml
Question 5
Create a file called requirements.yml in /home/sandy/ansible/roles to install two roles. The source
for the first role is geerlingguy.haproxy and geerlingguy.php. Name the first haproxy-role and the
second php-role. The roles should be installed in /home/sandy/ansible/roles.
Answer:
A
A. Explanation:
in /home/sandy/ansible/roles
vim requirements.yml
Run the requirements file from the roles directory:
ansible-galaxy install -r requirements.yml -p /home/sandy/ansible/roles
Question 6
Create a file called requirements.yml in /home/sandy/ansible/roles a file called role.yml in
/home/sandy/ansible/. The haproxy-role should be used on the proxy host. And when you curl
http://node3.example.com
it should display "Welcome to
node4.example.com
" and when you curl
again "Welcome to
node5.example.com
" The php-role should be used on the prod host.
Answer:
A
A. Explanation:
Solution as: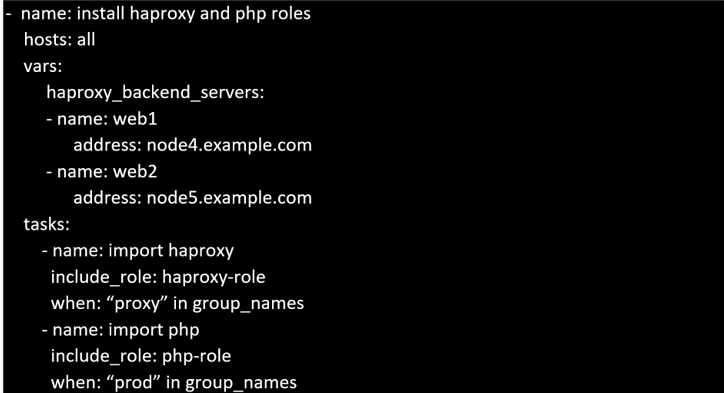
Check the proxy host by curl
http://node3.example.com
Question 7
Create an ansible vault password file called lock.yml with the password reallysafepw in the
/home/sandy/ansible directory. In the lock.yml file define two variables. One is pw_dev and the
password is 'dev' and the other is pw_mgr and the password is 'mgr' Create a regular file called
secret.txt which contains the password for lock.yml.
Answer:
A
A. Explanation:
ansible-vault create lock.yml
New Vault Password: reallysafepw
Confirm: reallysafepw
Question 8
Create the users in the file usersjist.yml file provided. Do this in a playbook called users.yml located
at /home/sandy/ansible. The passwords for these users should be set using the lock.yml file from
TASK7. When running the playbook, the lock.yml file should be unlocked with secret.txt file from
TASK 7.
All users with the job of 'developer' should be created on the dev hosts, add them to the group
devops, their password should be set using the pw_dev variable. Likewise create users with the job
of 'manager' on the proxy host and add the users to the group 'managers', their password should be
set using the pw_mgr variable.
Answer:
A
A. Explanation:
ansible-playbook users.yml vault-password-file=secret.txt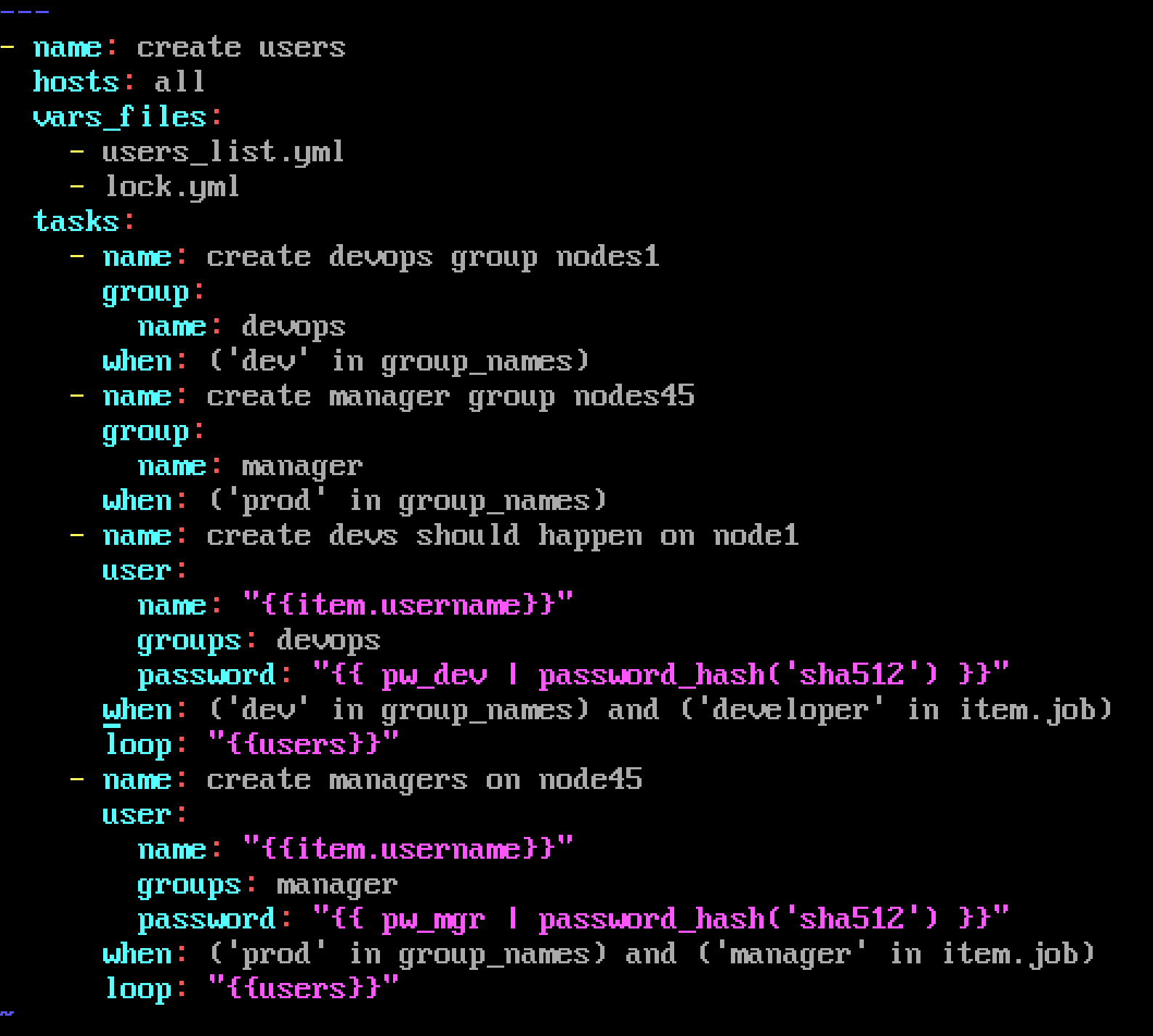
Question 9
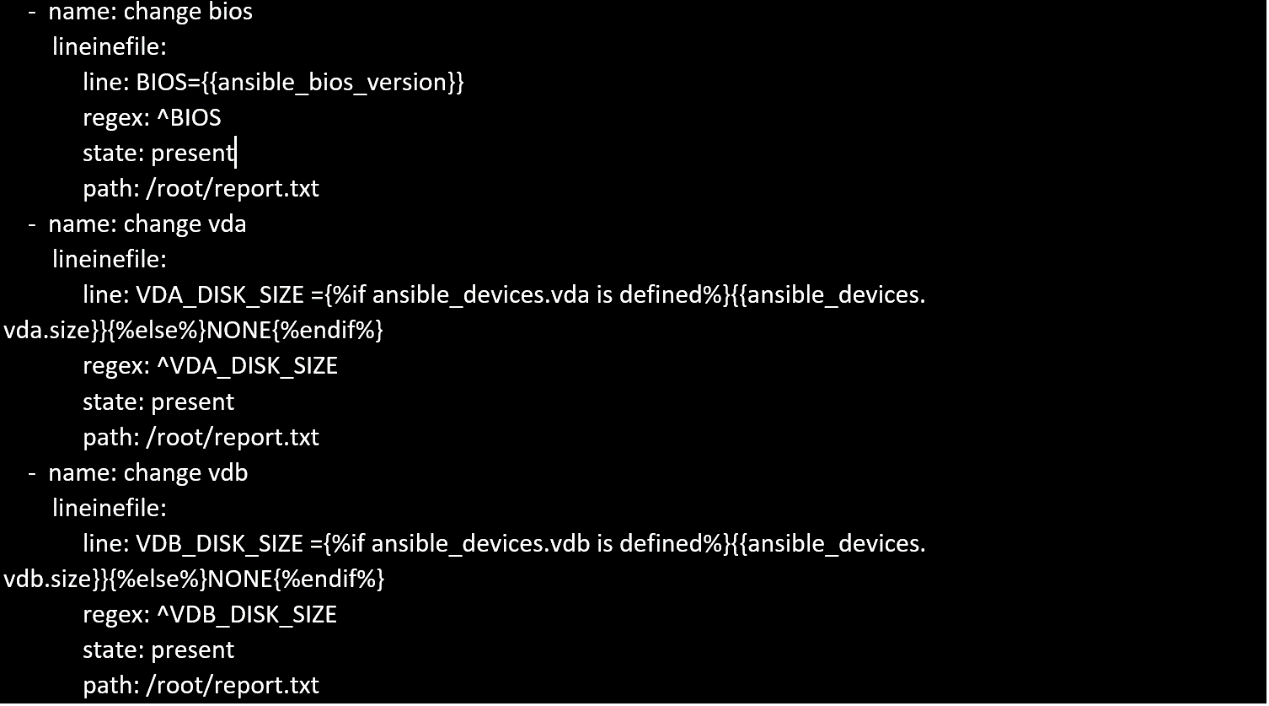
Create a file called specs.empty in home/bob/ansible on the local machine as follows:
HOST=
MEMORY=
BIOS=
VDA_DISK_SIZE=
VDB_DISK_SIZE=
Create the playbook /home/bob/ansible/specs.yml which copies specs.empty to all remote nodes'
path /root/specs.txt. Using the specs.yml playbook then edit specs.txt on the remote machines to
reflect the appropriate ansible facts.
Answer:
A
A. Explanation:
Solution as: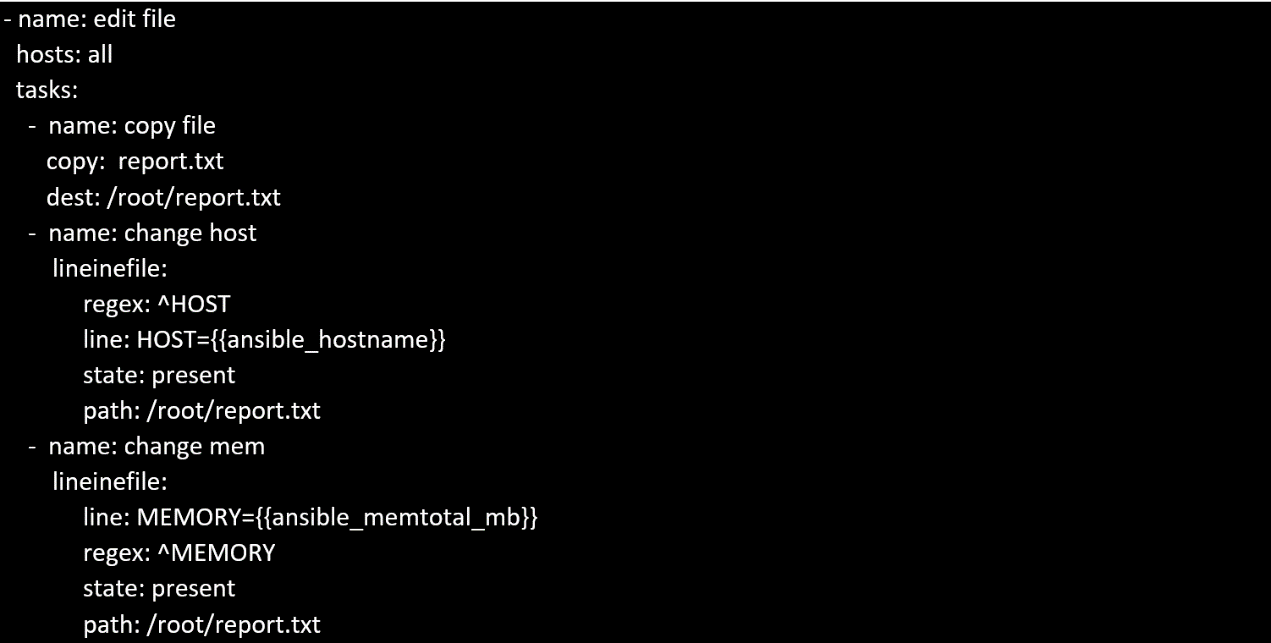
Question 10
Create a jinja template in /home/sandy/ansible/ and name it hosts.j2. Edit this file so it looks like the
one below. The order of the nodes doesn't matter. Then create a playbook in /home/sandy/ansible
called hosts.yml and install the template on dev node at /root/myhosts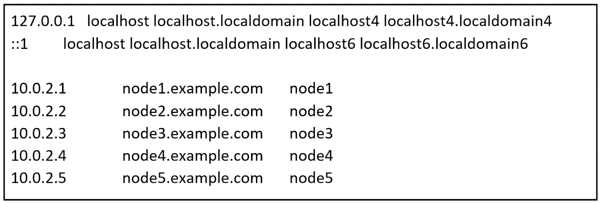
Answer:
A
A. Explanation:
Solution as: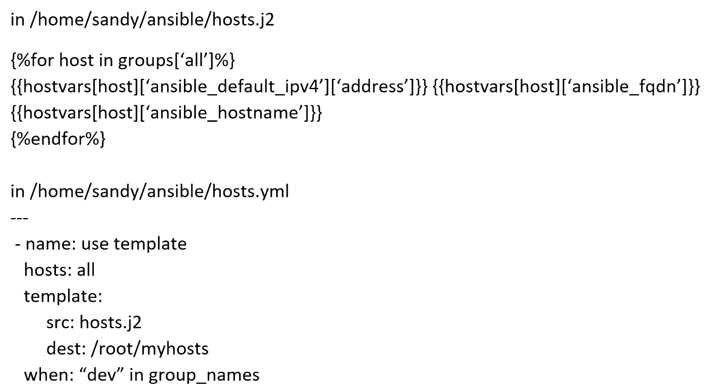
Question 11
In /home/sandy/ansible/ create a playbook called logvol.yml. In the play create a logical volume
called Iv0 and make it of size 1500MiB on volume group vgO If there is not enough space in the
volume group print a message "Not enough space for logical volume" and then make a 800MiB Iv0
instead. If the volume group still doesn't exist, create a message "Volume group doesn't exist" Create
an xfs filesystem on all Iv0 logical volumes. Don't mount the logical volume.
Answer:
A
A. Explanation:
Solution as: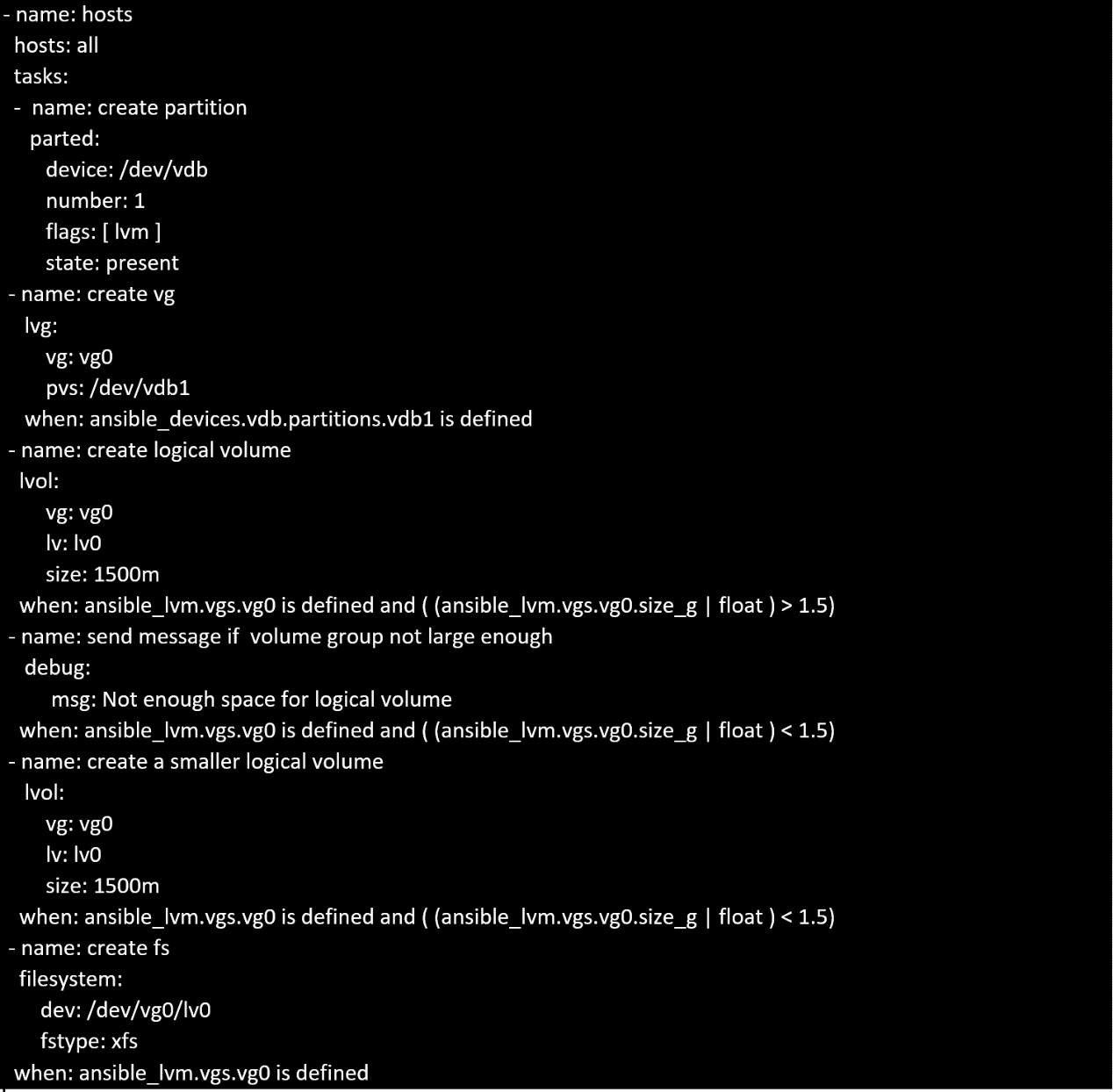
Question 12
Create a playbook called webdev.yml in 'home/sandy/ansible. The playbook will create a directory
Avcbdev on dev host. The permission of the directory are 2755 and owner is webdev. Create a
symbolic link from /Webdev to /var/www/html/webdev. Serve a file from Avebdev7index.html
which displays the text "Development" Curl
http://node1.example.com/webdev/index.html
to test
Answer:
A
A. Explanation:
Solution as: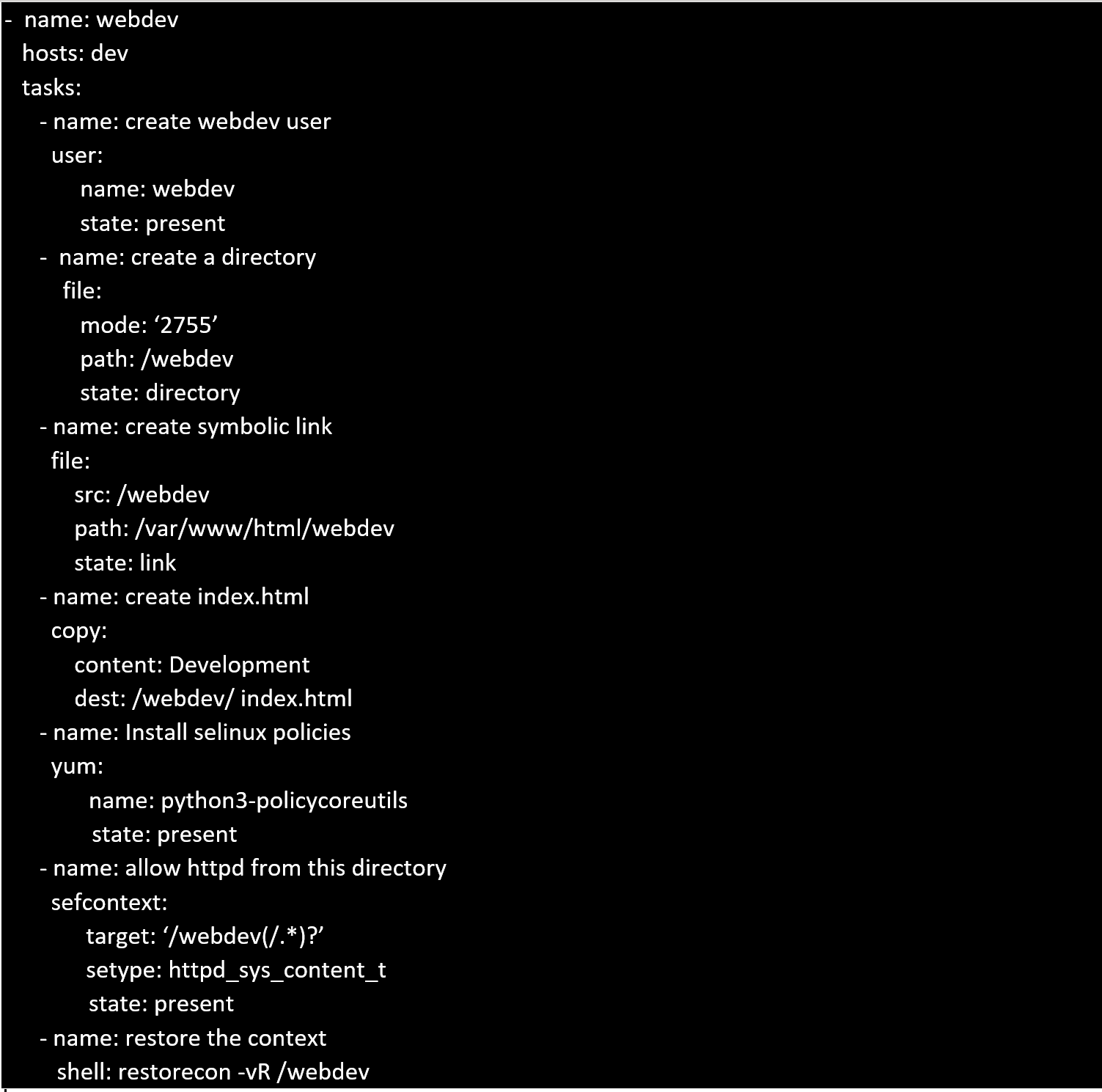
Question 13
Create a playbook called timesvnc.yml in /home/sandy/ansible using rhel system role timesync. Set
the time to use currently configured nip with the server 0.uk.
pool.ntp.org
. Enable burst. Do this on
all hosts.
Answer:
A
A. Explanation:
Solution as:
Question 14
Create a playbook called regulartasks.yml which has the system that append the date to
/root/datefile every day at noon. Name is job 'datejob'
Answer:
A
A. Explanation:
Solution as:
Question 15
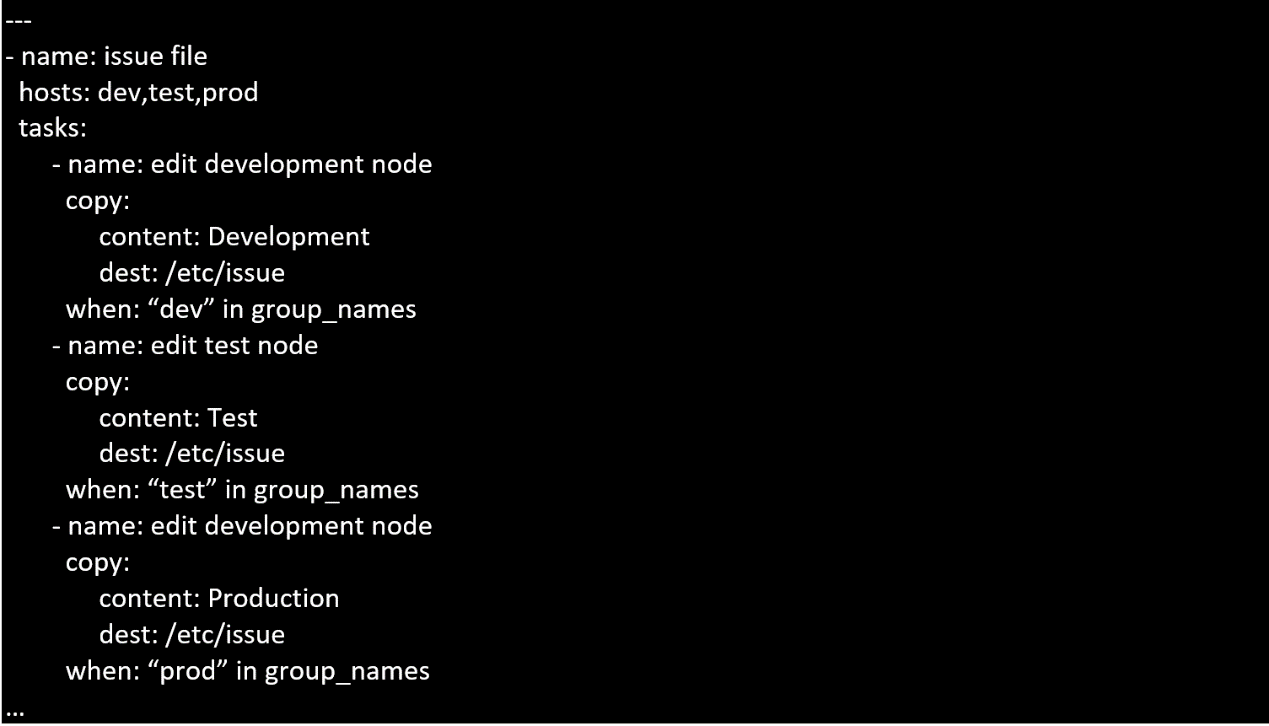
Create a playbook called issue.yml in /home/sandy/ansible which changes the file /etc/issue on all
managed nodes: If host is a member of (lev then write "Development" If host is a member of test
then write "Test" If host is a member of prod then write "Production"
Answer:
A
A. Explanation:
Solution as: