microsoft 98-366 Exam Questions
Questions for the 98-366 were updated on : Jun 29 ,2025
Page 1 out of 14. Viewing questions 1-15 out of 204
Question 1
This question requires that you evaluate the underlined text to determine if it is correct.
Plain old telephone service (POTS), most ISDN lines, and switched T1 lines are all examples of "Message Switching".
Select the correct answer if the underlined text does not make the statement correct. Select 'No change is needed'' if the
underlined text makes the statement correct.
- A. Circuit Switching
- B. Packet Switching
- C. FDDI Switching
- D. No change is needed
Answer:
A
Explanation:
* Examples of circuit-switched networks
Public switched telephone network (PSTN) ISDN B-channel
* You can get a circuit-switched T1, while frames clouds on T1s are usually packet-switched.
Question 2
The query protocol used to locate resources on a network is:
- A. User Datagram Protocol (UDP).
- B. Lightweight Directory Access Protocol (LDAP)
- C. Tracert
- D. Telnet.
Answer:
B
Explanation:
The Lightweight Directory Access Protocol (LDAP) is an open, vendor-neutral, industry standard application protocol for
accessing and maintaining distributed directory information services over an Internet Protocol (IP) network. Directory
services play an important role in developing intranet and Internet applications by allowing the sharing of information about
users, systems, networks, services, and applications throughout the network.
Question 3
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is
worth one point.
Hot Area:
Answer:

Explanation:
* No. IPv6 addresses are 128 bit in length. * No.No.
IPv6 addresses are written in eight groups of four hexadecimal digits separated by colons, such as
2001:0db8:85a3:0000:0000:8a2e:0370:7334.
Question 4
A network device that associates a Media Access Control (MAC) address with a port is a:
- A. DSL modem
- B. Hub
- C. Router
- D. Switch
Answer:
D
Explanation:
A switch begins learning the local MAC addresses as soon as it is connected to other devices or to a network. This learning
capability makes switches easy to use on a network.
The switch learning process works like this:
1.As a PC or other networked device sends a frame to another device through the switch, the switch captures the source
MAC address of the frame and the interface that received it.
2.The switch confirms or adds the MAC address and the port to the lookup table.
Question 5
When a client's DHCP-issued address expires, the client will:
- A. Select a new address and request approval from the DHCP server.
- B. Require manual configuration with a static IP address.
- C. Attempt to obtain a new address by broadcasting.
- D. Continue to use the address until it is notified to stop.
Answer:
C
Explanation:
Rebinding would occur.
Rebinding
If the DHCP client is unable to communicate with the DHCP server from which it obtained its lease, and 87.5 percent of its
lease time has expired, it will attempt to contact any available DHCP server by broadcasting DHCPRequest messages. Any
DHCP server can respond with a DHCPAck message, renewing the lease, or a DHCPNak message, forcing the DHCP client
to initialize and restart the lease process.
Note:
Renewing
IP addressing information is leased to a client, and the client is responsible for renewing the lease. By default, DHCP clients
try to renew their lease when 50 percent of the lease time has expired. To renew its lease, a DHCP client sends a
DHCPRequest message to the DHCP server from which it originally obtained the lease.
Reference: DHCP Client States in the Lease Process
Question 6
This question requires that you evaluate the underlined text to determine if it is correct.
All session data is "encrypted between all machines" while using telnet.
Select the correct answer if the underlined text does not make the statement correct. Select 'No change is needed" if the
underlined text makes the statement correct.
- A. Not encrypted
- B. Encrypted between any Windows machines
- C. Encrypted only to any non-Windows machines
- D. No change is needed
Answer:
A
Explanation:
Telnet, by default, does not encrypt any data sent over the connection (including passwords), and so it is often practical to
eavesdrop on the communications and use the password later for malicious purposes; anybody who has access to a router,
switch, hub or gateway located on the network between the two hosts where Telnet is being used can intercept the packets
passing by and obtain login, password and whatever else is typed with a packet analyzer.
Question 7
This question requires that you evaluate the underlined text to determine if it is correct.
In a wireless network that requires an SSL certificate, "WEP" handles the SSL certificate.
Select the correct answer if the underlined text does not make the statement correct. Select 'No change is needed" if the
underlined text makes the statement correct.
- A. 802.1X
- B. WPA2-PSK
- C. WPA-PSK
- D. No change is needed
Answer:
A
Explanation:
802.1x
This deployment scenario requires server certificates for each NPS server that performs 802.1X authentication.
Question 8
In local area network (LAN) topologies, the primary media access methods are: (Choose two.)
- A. Contention
- B. Negotiation
- C. Kerberos
- D. Token passing
Answer:
A D
Explanation:
Media contention occurs when two or more network devices have data to send at the same time. Because multiple devices
cannot talk on the network simultaneously, some type of method must be used to allow one device access to the network
media at a time. This is done in two main ways: carrier sense multiple access collision detect (CSMA/CD) and token passing.
Question 9
What is the maximum cable length for a single Cat5 UTP cable run?
- A. 285 feet/86.87 meters
- B. 328 feet/99.97 meters
- C. 432 feet/131.67 meters
- D. 600 feet/182.88 meters
Answer:
B
Explanation:
Cat5/5e/6 Ethernet Copper Cabling has a Maximum Segment Length of 100 Meters.
Question 10
What are two characteristics of the CSMA/CD access method? (Choose two.)
- A. It checks to see if a collision has been detected.
- B. It does a round robin search for requests to transmit from all nodes on the network.
- C. It signals its intent to transmit on the network.
- D. It waits until the transmission medium is idle.
Answer:
A D
Explanation:
Main procedure for the CSMA/CD:
1. Is my frame ready for transmission? If yes, it goes on to the next point. 2. Is medium idle? If not, wait until it becomes
ready 3. Start transmitting.
4. Did a collision occur? If so, go to collision detected procedure.
5. Reset retransmission counters and end frame transmission.
Note:
Carrier Sense Multiple Access With Collision Detection (CSMA/CD) is a media access control method used most notably in
local area networking using early Ethernet technology. It uses a carrier sensing scheme in which a transmitting data station
detects other signals while transmitting a frame, and stops transmitting that frame, transmits a jam signal, and then waits for
a random time interval before trying to resend the frame.
Question 11
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is
worth one point.
Hot Area:
Answer:

Explanation:
* Dynamic Routing. A router with dynamically configured routing tables is known as a dynamic router. Dynamic routing
consists of routing tables that are built and maintained automatically through an ongoing communication between routers.*
Most of the dominant routing algorithms are dynamic routing algorithms, which adjust to changing network circumstances by
analyzing incoming routing update messages. If the message indicates that a network change has occurred, the routing
software recalculates routes and sends out new routing update messages. These messages permeate the network,
stimulating routers to rerun their algorithms and change their routing tables accordingly.
* When there are multiple routes to the same destination, a router must have a mechanism for calculating the best path. A
metric is a variable assigned to routes as a means of ranking them from best to worst or from most preferred to
leastpreferred.
Question 12
DRAG DROP
Match the VPN connection type to the corresponding definition.
To answer, drag the appropriate VPN term from the column on the left to its definition on the right. Each term may be used
once, more than once, or not at all. Each correct match is worth one point.
Select and Place: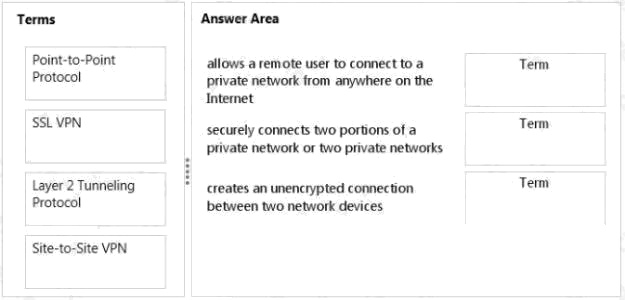
Answer:
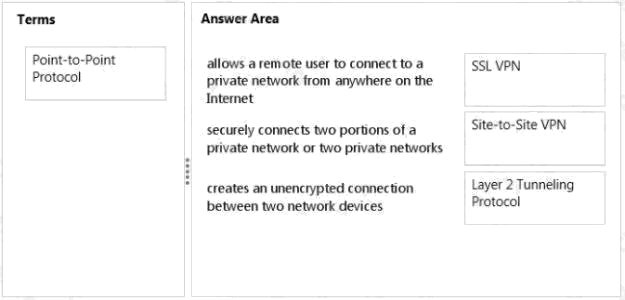
Explanation:
* An SSL VPN (Secure Sockets Layer virtual private network) is a form of VPN that can be used with a standard Web
browser. In contrast to the traditional Internet Protocol Security (IPsec) VPN, an SSL VPN does not require the installation
ofspecialized client software on the end user's computer. It's used to give remote users with access to Web applications,
client/server applications and internal network connections.
* A site-to-site VPN allows offices in multiple fixed locations to establish secure connections with each other over a public
network such as the Internet.
* Layer 2 Tunneling Protocol (L2TP) is a tunneling protocol used to support virtual private networks (VPNs) or as part of the
delivery of services by ISPs. It does not provide any encryption or confidentiality by itself.
Question 13
HOTSPOT
Your network uses routers configured with the RIP router protocol.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:

Explanation:
Routing Information Protocol (RIP) uses hop count as the metric to rate the value of different routes. The hop count is the
number of devices that can be traversed in a route. A directly connected network has a metric of zero; an unreachable
network has a metric of 16. This limited metric range makes RIP unsuitable for large networks.
The Routing Information Protocol (RIP) sends routing-update messages at regular intervals and when the network topology
changes. When a device receives a RIP routing update that includes changes to an entry, the device updates its routing
table to reflect the new route. The metric value for the path is increased by 1, and the sender is indicated as the next hop.
RIP devices maintain only the best route (the route with the lowest metric value) to a destination. After updating its routing
table, the device immediately begins transmitting RIP routing updates to inform other network devices of the change. These
updates are sent independently of the regularly scheduled updates that RIP devices send.
Summarizing routes in RIP Version 2 improves scalability and efficiency in large networks. Summarizing IP addresses
means that there is no entry for child routes (routes that are created for any combination of the individual IP addresses
contained within a summary address) in the RIP routing table, reducing the size of the table and allowing the router to handle
more routes.
It is a stable protocol that uses a distance-vector algorithm to calculate routes.
References:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/iproute_rip/configuration/15-mt/irr-15-mt-book/irr-cfg-info-prot.html
Question 14
Which protocol is a transport layer protocol?
- A. FTP
- B. IP
- C. UDP
- D. ASCII
Answer:
C
Explanation:
Transport layer protocols include: UDP, TCP
Question 15
The protocol that maps IP addresses to a Media Access Control (MAC) address is:
- A. Internet Message Access Protocol (IMAP).
- B. Dynamic Host Configuration Protocol (DHCP).
- C. Routing Information Protocol (RIP).
- D. User Datagram Protocol (UDP).
- E. Address Resolution Protocol (ARP).
Answer:
E
Explanation:
Address Resolution Protocol (ARP) is a protocol for mapping an Internet Protocol address (IP address) to a physical
machine address (MAC address) that is recognized in the local network.