IBM C9510-401 Exam Questions
Questions for the C9510-401 were updated on : Dec 20 ,2025
Page 1 out of 5. Viewing questions 1-15 out of 73
Question 1
An application contains a web services client and the application is deployed and running. A system
administrator has to add a response timeout to the deployed web services client, so the call fails in a
timely fashion.
Which artifact should the administrator use?
- A. web.xml
- B. was-webservices-sca.xml
- C. ibm-webservices-bnd.xml
- D. ibm-webservicesclient-bnd.xml
Answer:
D
Explanation:
The ibm-webservicesclient-bnd.xmi deployment descriptor file contains information for the web
services run time that is WebSphere product-specific. This deployment descriptor file is used with
Java API for XML-based web services.
References:
https://www.ibm.com/support/knowledgecenter/SSEQTJ_8.5.5/com.ibm.websphere.base.doc/ae/rwbs_assembpropclient.html
Question 2
A system administrator has started a Liberty profile server using the default values. Later, the
administrator modified the server.xml file for the server to include
<applicationMonitor updateTrigger=polled pollingRate=100ms
dropins=${server.config.dir}/applications dropinsEnabled=true/>
The administrator placed the application ServletApp.war in the apps directory under
${server.config.dir}. While accessing the correct URL for the home page of the application, the error
Context Root Not Found occurs in the browser.
How can the administrator resolve this error?
- A. Restart the Liberty profile server.
- B. Install the ServletApp.war file using the Integrated Solutions Console (ISC).
- C. Place the ServletApp.war file in the directory named dropins under ${server.config.dir}.
- D. Place the ServletApp.war file in the directory named applications under ${server.config.dir}.
Answer:
D
Question 3
A developer created an enterprise application which contained data source and security role
information. The developer asked a system administrator to install this application to an application
server where global security is enabled using the Integrated Solutions Console (ISC). A new data
source was configured at the server scope for the use of this application. While load testing the
application, the developer noticed that the attributes configured on the new data source were
ignored by the application server.
How can the administrator ensure that the attributes configured on the new data source are used by
the application server?
- A. Create the data source under cell scope instead of server scope.
- B. Delete any data source of the same name defined under node, cluster or cell scope.
- C. Reinstall the application and clear the Process embedded configuration check box.
- D. Correct the component-managed and container-managed authentication aliases set on the data source.
Answer:
C
Explanation:
Process embedded configuration
Specifies whether the embedded configuration should be processed. An embedded configuration
consists of files such as resource.xml, variables.xml, and deployment.xml. You can collect WebSphere
Application Server-specific deployment information and store it in the application EAR file. Such an
EAR file can then be installed into a WebSphere Application Server configuration, using application
management interfaces that are described in the topic, Installing an application through
programming.
One such application EAR file is an enhanced EAR file, which is created when you export an already
installed application. The embedded configuration check box identifies such an enhanced EAR file. By
default, the check box for "process embedded configuration" is checked if the application is detected
to be an enhanced EAR. The application install options are prepopulated with the information from
the embedded configuration whether the check box for "process embedded configuration" is
checked or not. Users can overwrite these values during the deployment process.
References:
https://www.ibm.com/support/knowledgecenter/SSAW57_8.0.0/com.ibm.websphere.nd.doc/info/ae/ae/urun_rapp_installoptions.html
Question 4
After installing an enhanced EAR in a WebSphere Application Server environment, a system
administrator with Configurator privileges is able to see a JDBC provider and a data source in the
Integrated Solution Console (ISC) but is not able to delete these resources.
How can the administrator resolve this issue?
- A. Use the AdminTask object to delete the resources.
- B. Stop all application server instances and then delete the resources.
- C. Ask another administrator with iscadmin privilege to delete the resource.
- D. Edit the EAR to remove the application scoped resources and reinstall the application.
Answer:
A
Explanation:
The JDBCProviderManagement command group for the AdminTask object includes the following
commands:
References:
https://www.ibm.com/support/knowledgecenter/en/SSAW57_8.5.5/com.ibm.websphere.nd.doc/ae/rxml_atjdbcprovider.html
Question 5
The administrator needs to identify any security role references and security constraints in a web
application.
How can the administrator identify these roles and constraints?
- A. ibm-application-ext.xml file using a text editor.
- B. ibmconfig folder in the application after using the EARExpander command.
- C. Web deployment descriptor using IBM Assembly and Deploy Tools.
- D. Security role to user/group mapping by using the Integrated Solutions Console (ISC).
Answer:
C
Explanation:
Securing web applications using an assembly tool.
You can use three types of web login authentication mechanisms to configure a web application:
basic authentication, form-based authentication and client certificate-based authentication. Protect
web resources in a web application by assigning security roles to those resources.
References:
https://www.ibm.com/support/knowledgecenter/SS7JFU_8.5.5/com.ibm.websphere.nd.doc/ae/tsec_secweb_atk.html
Question 6
A system administrator needs to configure a JDBC provider and a data source for an application in a
clustered environment. The administrator also needs to copy the JDBC drivers from the database
server to the application server machines.
How can the administrator meet these requirements?
- A. Create a JDBC provider and the data source in the cluster scope.Copy the driver to all nodes.Set the environment variable at the node level to the drivers path.
- B. Create a JDBC provider in the server scope and the data source in the node scope.Copy the driver to all application servers.Set the environment variable at the node level to the drivers path.
- C. Create a JDBC provider in the node scope and the data source in the cell scope.Copy the driver to the deployment manager.Set the environment variable at the server level to point to the deployment manager path.
- D. Create a JDBC provider in the application scope and the data source in the server scope.Copy the driver to all application server directories.Set the environment variable in each JVM to the drivers path.
Answer:
A
Question 7
A system administrator has configured a cluster containing 40 servers. The cluster members all
belong to one core group. While examining the log files, the administrator notices that the core
group coordinator is consuming abnormally high amounts of memory and CPU resources.
How can the system administrator reduce the memory and CPU resource usage of the core group
coordinator?
- A. Configure a core group bridge.
- B. Configure a second active coordinator.
- C. Decrease the memory on the machine.
- D. Move the coordinator to another machine.
Answer:
B
Explanation:
Remember that coordinator election occurs whenever the view changes. Electing a new coordinator
uses a lot of resources because this process causes increased network traffic and CPU consumption.
Specifying a preferred coordinator server, whenever practical, helps eliminate the need to make
frequent coordinator changes.
References:
https://www.ibm.com/support/knowledgecenter/SSAW57_8.5.5/com.ibm.websphere.nd.doc/ae/crun_ha_coordinator.html
Question 8
A system administrator has created a cluster containing two servers in a same node. The
administrator did not select the option Generate unique HTTP ports during the creation of the cluster
members. After the cluster creation, the administrator changed the HTTP port of the second cluster
member to 9081.
Testing the servers using the snoop servlet directly to the servers HTTP port, the administrator got
the following error message for the second server: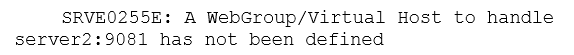
How can the administrator fix this problem?
- A. Regenerate and propagate the HTTP plug-in.
- B. Add the port 9081 to the default_host alias.
- C. Create a new virtual host alias at the cell level for the port 9081.
- D. Edit the server.xml for the second server and add the port 9081.
Answer:
B
Explanation:
Problem(Abstract)
When setting up IBM Cognos within IBM WebSphere, the URI is not accessible. The error message
when trying the Error! Hyperlink reference not valid. port>/p2pd/servlet/dispatch is
SRVE0255E: A WebGroup/Virtual Host to handle /p2pd/servlet/dispatch has not been defined.
Symptom
Unable to start IBM Cognos Business Intelligence
Cause
The virtual host does not contain IBM WebSphere Port that the Application server is listening on. This
may be one of several reasons.
References: http://www-01.ibm.com/support/docview.wss?uid=swg21438842
Question 9
A web application is hosted on an application server that receives HTTP requests from a third party
application named myApp. The URIGroup mapping for this application is called default_host_myApp.
The development team asks a system administrator to configure the HTTP plug-in to prevent routing
requests to any application server except server1.
The following exhibit shows the parts of the plugin-cfg.xml file that are relevant for myApp. The
UriGroups for other applications are not shown in the exhibit.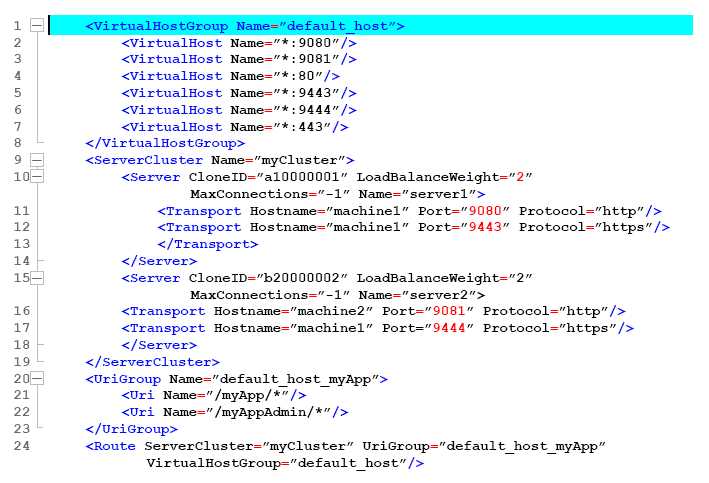
What should the administrator do to the plugin-cfg.xml file to ensure that requests for
default_host_myApp URIGroup are routed only to machine1?
- A. Delete the Server tag for CloneId=”b20000002”Delete all of the tags within the Server tag
- B. Delete the UriGroup tag for default_host_myAppDelete all of the tags within the UriGroup tag
- C. Delete the VirtualHostGroup tag for default_hostDelete all of the tags within the VirtualHostGroup tag
- D. Edit the LoadBalanceWeight for server1 to 20Edit the LoadBalanceWeight for server2 to 2
Answer:
A
Question 10
A system administrator needs to set a new Liberty profile environment to support an application.
What should the administrator do to enable this environment for high availability and scalability of
the application?
- A. Define multiple server members in one collective controller.
- B. Define multiple servers in a cluster in one collective controller.
- C. Define multiple collective controllers within a Liberty collective.
- D. Define multiple server members in multiple collective controllers.
Answer:
B
Explanation:
Setting up Liberty server clusters
A Liberty can be configured into a server cluster for application high availability and scale.
The collectiveController-1.0 feature and its capabilities are available only in multiple-server products
such as WebSphere Application Server Liberty Network Deployment and WebSphere Application
Server Liberty for z/OS. The feature is not available in single-server products such as WebSphere
Application Server Liberty, WebSphere Application Server Liberty - Express, or WebSphere
Application Server Liberty Core. If you have a multiple-server product installation, you can use its
collectiveController-1.0 feature to work with collective members from single-server products.
References:
https://www.ibm.com/support/knowledgecenter/en/SSAW57_8.5.5/com.ibm.websphere.wlp.nd.doc/ae/cwlp_server_clusters.html
Question 11
A system administrator has added a server cluster as a member of a service integration bus (SIB). The
administrator needs to configure one messaging engine for each server in this cluster and to have a
failover location for each messaging engine.
What should the administrator do to achieve the required design?
- A. Configure a new messaging engine in each server to support failover.
- B. Configure the data store for each messaging engine for each server in the cluster.
- C. Select scalability with high availability as the messaging engine policy.
- D. Create a core group policy to restrict each messaging engine to a particular server.
Answer:
C
Explanation:
The scalability with high availability configuration ensures that there is a messaging engine for each
server in a cluster, and that each messaging engine has a failover location.
References:
Question 12
A web application was deployed on a WebSphere Application Server cluster. While users are using
the application, one of the cluster servers fails and the users lose their working data.
What can the system administrator configure to ensure users can continue to work if one of the
cluster server fails?
- A. An increased session timeout.
- B. A cluster of external HTTP servers.
- C. A load balancer to spread work between existing servers.
- D. A WebSphere eXtreme Scale HTTP session management.
Answer:
D
Explanation:
WebSphere eXtreme Scale can dynamically process, partition, replicate, and manage application data
and business logic across hundreds of servers. It provides transactional integrity and transparent fail-
over to ensure high availability, high reliability, and consistent response times.
References:
http://www.ibm.com/developerworks/websphere/techjournal/1301_ying/1301_ying.html
Question 13
A system administrator ran the backupConfig command to backup the configuration using the
nostop option. The administrator changed the properties for the service integration environment by
modifying the sib.properties file. During testing the administrator noticed Service Integration Bus
related errors and wanted to restore the service integration environment. The administrator used the
restoreConfig command, but the tuning properties for the service integration environment were not
restore.
How can the administrator prevent this issue?
- A. Use full repository checkpoint for both the backup and the restore.
- B. Use the restoreConfig command with –nostop for the restore.
- C. Use the manageprofiles command for both the backup and the restore.
- D. Use the backupConfig command without –nostop for the backup
- E. Use the restoreConfig command without –nostop for the restore.
Answer:
A
Explanation:
With the repository checkpoint and restore function, you can back up copies of files from the master
configuration repository. You can use the backups to restore the configuration to a previous state if
future configuration changes cause operational problems. By using this function, you can reduce
recovery time for problems that are caused by configuration changes. Studies of unplanned outages
have shown that as much as 36 percent of unplanned outages are due to operator errors. A common
source of operator error is a bad configuration change. The ability to quickly undo a bad
configuration change is critical to minimizing the outage window.
References:
https://www.ibm.com/support/knowledgecenter/SSAW57_8.5.5/com.ibm.websphere.nd.doc/ae/cwve_xdsochckpt.html
Question 14
A system administrator needs to install WebSphere Application Server using response files, so that a
silent install can be done. The administrator has ensured that all required prerequisites have already
been installed and, has downloaded and expanded the required WebSphere Application Server
installation files.
What can the administrator run to install the product?
- A. install –options responsefile.xml -silent
- B. install –acceptLicense –options responsefile.xml -silent
- C. imcl –acceptLicense input responsefile.xml –log logfile.txt
- D. IBMIM –acceptLicense –input responsefile.xml –log logfile.txt
Answer:
C
Explanation:
Example of the use of the response files to install the product.
imcl.exe -acceptLicense
input C:\temp\keyring_response_file.xml
-log C:\temp\keyring_log.xml
References:
Question 15
A system administrator completed a WebSphere Application Server installation by using the
Installation Manager. During installation, all defaults were selected for the installation root
directories and the shared resources directory. Over time, the administrator has updated the
installation with various interim fixes and fix packs. The administrator notices that the shared
resources directory is very large in size and grows larger each time the Installation Manager is run.
How can the administrator decrease the size and remove some of the content from the shared
resources directory?
- A. Manually delete content from the directory.
- B. During an update, create a new shared resources directory.
- C. Clear the Delete Saved Files option for the Installation Manager.
- D. Set the preserveDownloadedArtifacts preference to false.
Answer:
D
Explanation:
Because product payloads are cached in this directory, space requirements can grow very large over
the lifetime of the product, as service updates are applied. The WebSphere Application Server
product image is large, so if this content is permitted to accumulate, then this directory will grow to
be many gigabytes in size over the course of multiple fix pack applications. You should never
manually delete the content in this folder. Instead, during any installation or maintenance operation,
you can specify the following preference to remove some of the content in this folder:
preferences com.ibm.cic.common.core.preferences.preserveDownloadedArtifacts=false
References:
https://www.ibm.com/support/knowledgecenter/en/SSAW57_7.0.0/com.ibm.websphere.installation.soafepnd.doc/info/ae/ae/tins_installfp_dist.html