Fortinet NSE5-FCT-7-0 Exam Questions
Questions for the NSE5-FCT-7-0 were updated on : Apr 19 ,2025
Page 1 out of 5. Viewing questions 1-10 out of 44
Question 1
An administrator wants to simplify remote access without asking users to provide user credentials.
Which access control method provides this solution?
- A. ZTNA full mode
- B. SSL VPN
- C. L2TP
- D. ZTNA IP/MAC filtering mode
Answer:
a
Question 2
An administrator installs FortiClient on Windows Server.
What is the default behavior of real-time protection control?
- A. Real-time protection must update AV signature database.
- B. Real-time protection is disabled.
- C. Real-time protection sends malicious files to FortiSandbox when the file is not detected locally.
- D. Real-time protection must update the signature database from FortiSandbox.
Answer:
b
Question 3
Refer to the exhibit.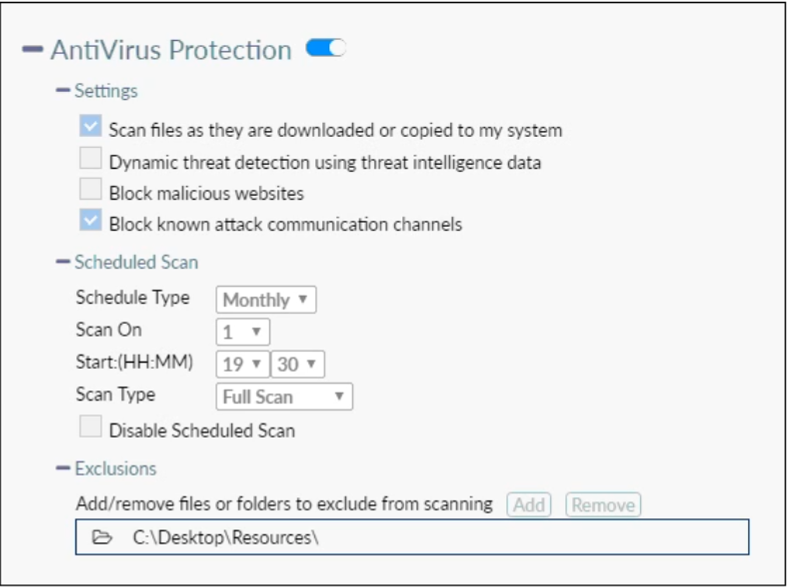
Based on the settings shown in the exhibit, which statement about FortiClient behaviour is true?
- A. FortiClient blocks and deletes infected files after scanning them.
- B. FortiClient copies infected files to the Resources folder without scanning them.
- C. FortiClient quarantines infected files and reviews later, after scanning them.
- D. FortiClient scans infected files when the user copies files to the Resources folder.
Answer:
a
Question 4
Refer to the exhibit.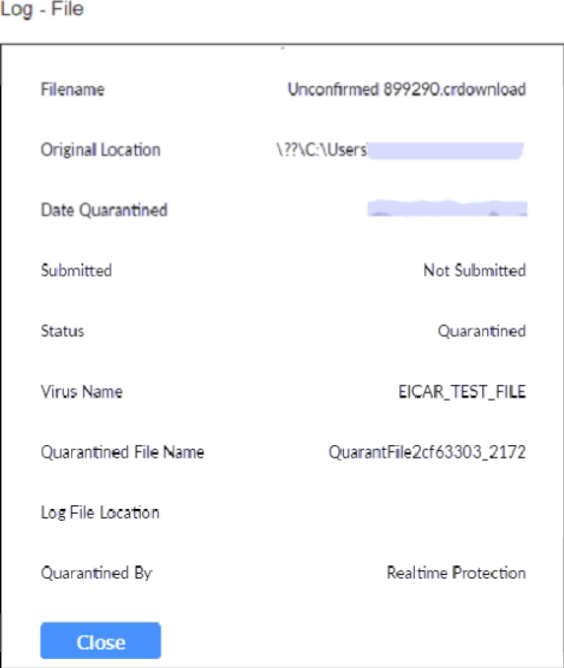
Based on the FortiClient log details shown in the exhibit, which two statements are true? (Choose two.)
- A. The filename is sent to FortiSandbox for further inspection.
- B. The file status is Quarantined.
- C. The file location is \??\D:\Users\.
- D. The filename is Unconfirmed 899290.crdownload.
Answer:
bd
Question 5
Which statement about the FortiClient enterprise management server is true?
- A. It receives the configuration information of endpoints from FortiGate.
- B. It provides centralized management of multiple endpoints running FortiClient software.
- C. It receives the CA certificate from FortiGate to validate client certificates.
- D. It enforces compliance on the endpoints using tags.
Answer:
b -
Question 6
Refer to the exhibit, which shows the Zero Trust Tagging Rule Set configuration.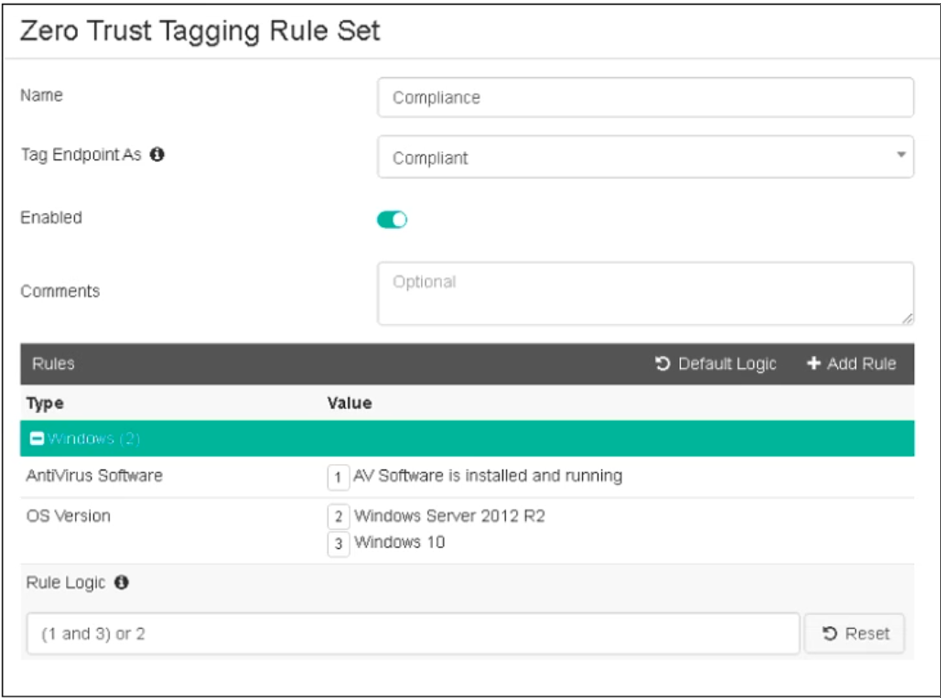
Which two statements about the rule set are true? (Choose two.)
- A. The endpoint must satisfy that only Windows 10 is running.
- B. The endpoint must satisfy that only AV software is installed and running.
- C. The endpoint must satisfy that antivirus is installed and running and Windows 10 is running.
- D. The endpoint must satisfy that only Windows Server 2012 R2 is running.
Answer:
bc
Question 7
An administrator needs to connect FortiClient EMS as a fabric connector to FortiGate.
What is the prerequisite to get FortiClient EMS to connect to FortiGate successfully?
- A. Import and verify the FortiClient EMS root CA certificate on FortiGate.
- B. Revoke and update the FortiClient client certificate on EMS.
- C. Revoke and update the FortiClient EMS root CA.
- D. Import and verify the FortiClient client certificate on FortiGate.
Answer:
a
Question 8
Which two statements are true about ZTNA? (Choose two.)
- A. ZTNA provides role-based access.
- B. ZTNA manages access for remote users only.
- C. ZTNA manages access through the client only.
- D. ZTNA provides a security posture check.
Answer:
ad
Question 9
Which two third-party tools can an administrator use to deploy FortiClient? (Choose two.)
- A. Microsoft Active Directory GPO
- B. Microsoft SCCM
- C. QR code generator
- D. Microsoft Windows Installer
Answer:
ab
Question 10
Which two statements are true about the ZTNA rule? (Choose two.)
- A. It enforces access control.
- B. It redirects the client request to the access proxy.
- C. It applies security profiles to protect traffic.
- D. It defines the access proxy.
Answer:
bc