comptia PT0-002 Exam Questions
Questions for the PT0-002 were updated on : Dec 15 ,2025
Page 1 out of 26. Viewing questions 1-10 out of 255
Question 1
Which of the following protocols or technologies would in-transit confidentially protection for emailing the final security assessment report?
- A. S/MIME
- B. FTPS
- C. DNSSEC
- D. AS2
Answer:
a
Question 2
A penetration tester is starting an assessment but only has publicly available information about the target company. The client is aware of this exercise and is preparing for the test.
Which of the following describes the scope of the assessment?
- A. Partially known environment testing
- B. Known environment testing
- C. Unknown environment testing
- D. Physical environment testing
Answer:
c
Question 3
A penetration tester is reviewing the following DNS reconnaissance results for comptia.org from dig:
...
;; ANSWER SECTION
comptia.org. 3569 IN MX comptia.org-mail.protection.outlook.com. comptia.org. 3569 IN A 3.219.13.186. comptia.org. 3569 IN NS ns1.comptia.org. comptia.org. 3569 IN SOA haven. administrator.comptia.org. comptia.org. 3569 IN MX new.mx0.comptia.org. comptia.org. 3569 IN MX new.mx1.comptia.org.
Which of the following potential issues can the penetration tester identify based on this output?
- A. At least one of the records is out of scope.
- B. There is a duplicate MX record.
- C. The NS record is not within the appropriate domain.
- D. The SOA records outside the comptia.org domain.
Answer:
b
Question 4
HOTSPOT You are a security analyst tasked with hardening a web server. You have been given a list of HTTP payloads that were flagged as malicious.
INSTRUCTION Giving the following attack signatures, determine the attack type, and then identify the associated remediation to prevent the attack in the future.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Hot Area:
Answer:
None

Question 5
A penetration tester needs to access a building that is guarded by locked gates, a security team, and cameras. Which of the following is a technique the tester can use to gain access to the IT framework without being detected?
- A. Pick a lock.
- B. Disable the cameras remotely.
- C. Impersonate a package delivery worker.
- D. Send a phishing email.
Answer:
c
Question 6
A penetration tester is conducting a penetration test and discovers a vulnerability on a web server that is owned by the client. Exploiting the vulnerability allows the tester to open a reverse shell. Enumerating the server for privilege escalation, the tester discovers the following: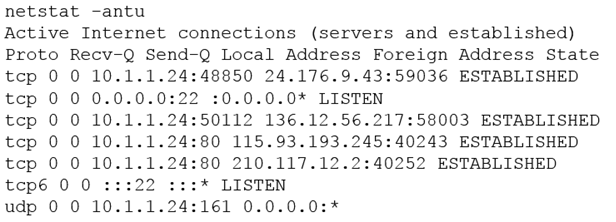
Which of the following should the penetration tester do NEXT?
- A. Close the reverse shell the tester is using.
- B. Note this finding for inclusion in the final report.
- C. Investigate the high numbered port connections.
- D. Contact the client immediately.
Answer:
d
Question 7
Which of the following provides a matrix of common tactics and techniques uses by attackers along with recommended mitigations?
- A. NIST SP 800-53
- B. OWASP Top 10
- C. MITRE ATT&CK framework
- D. PTES technical guidelines
Answer:
c
Question 8
A penetration tester has obtained shell access to a Windows host and wants to run a specially crafted binary for later execution using the ymic.exe process call create function. Which of the following OS or filesystem mechanisms is MOST likely to support this objective?
- A. Alternate data streams
- B. PowerShell modules
- C. MP4 steganography
- D. ProcMon
Answer:
d
Question 9
A penetration tester initiated the transfer of a large data set to verify a proof-of-concept attack as permitted by the ROE. The tester noticed the client's data included PII, which is out of scope, and immediately stopped the transfer. Which of the following MOST likely explains the penetration tester's decision?
- A. The tester had the situational awareness to stop the transfer.
- B. The tester found evidence of prior compromise within the data set.
- C. The tester completed the assigned part of the assessment workflow.
- D. The tester reached the end of the assessment time frame.
Answer:
a
Question 10
A penetration tester ran the following commands on a Windows server: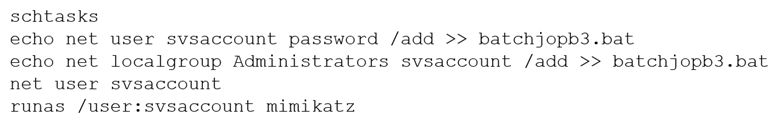
Which of the following should the tester do AFTER delivering the final report?
- A. Delete the scheduled batch job.
- B. Close the reverse shell connection.
- C. Downgrade the svsaccount permissions.
- D. Remove the tester-created credentials.
Answer:
c