comptia CAS-004 Exam Questions
Questions for the CAS-004 were updated on : Sep 09 ,2025
Page 1 out of 37. Viewing questions 1-10 out of 361
Question 1
A hospitality company experienced a data breach that included customer PII. The hacker used social engineering to convince an employee to grant a third-party application access to some company documents within a cloud file storage service Which of the following is the BEST solution to help prevent this type of attack in the future?
- A. NGFW for web traffic inspection and activity monitoring
- B. CSPM for application configuration control
- C. Targeted employee training and awareness exercises
- D. CASB for OAuth application permission control
Answer:
d
Question 2
A local university that has a global footprint is undertaking a complete overhaul of its website and associated systems Some of the requirements are:
Handle an increase in customer demand of resources
Provide quick and easy access to information
Provide high-quality streaming media
Create a user-friendly interface
Which of the following actions should be taken FIRST?
- A. Deploy high-availability web servers.
- B. Enhance network access controls.
- C. Implement a content delivery network.
- D. Migrate to a virtualized environment.
Answer:
a
Question 3
A company is migrating from company-owned phones to a BYOD strategy for mobile devices. The pilot program will start with the executive management team and be rolled out to the rest of the staff in phases. The company's Chief Financial Officer loses a phone multiple times a year.
Which of the following will MOST likely secure the data on the lost device?
- A. Require a VPN to be active to access company data.
- B. Set up different profiles based on the person's risk.
- C. Remotely wipe the device.
- D. Require MFA to access company applications.
Answer:
c
Question 4
An organization requires a legacy system to incorporate reference data into a new system. The organization anticipates the legacy system will remain in operation for the next 18 to 24 months. Additionally, the legacy system has multiple critical vulnerabilities with no patches available to resolve them. Which of the following is the BEST design option to optimize security?
- A. Limit access to the system using a jump box.
- B. Place the new system and legacy system on separate VLANs.
- C. Deploy the legacy application on an air-gapped system.
- D. Implement MFA to access the legacy system.
Answer:
a
Question 5
A security analyst for a managed service provider wants to implement the most up-to-date and effective security methodologies to provide clients with the best offerings. Which of the following resources would the analyst MOST likely adopt?
- A. OSINT
- B. ISO
- C. MITRE ATT&CK
- D. OWASP
Answer:
c
Question 6
An energy company is required to report the average pressure of natural gas used over the past quarter. A PLC sends data to a historian server that creates the required reports.
Which of the following historian server locations will allow the business to get the required reports in an and IT environment?
- A. In the environment, use a VPN from the IT environment into the environment.
- B. In the environment, allow IT traffic into the environment.
- C. In the IT environment, allow PLCs to send data from the environment to the IT environment.
- D. Use a screened subnet between the and IT environments.
Answer:
c
Question 7
Technicians have determined that the current server hardware is outdated, so they have decided to throw it out.
Prior to disposal, which of the following is the BEST method to use to ensure no data remnants can be recovered?
- A. Drive wiping
- B. Degaussing
- C. Purging
- D. Physical destruction
Answer:
b
Reference:
https://securis.com/data-destruction/degaussing-as-a-service/
Question 8
A company would like to obfuscate PII data accessed by an application that is housed in a database to prevent unauthorized viewing. Which of the following should the company do to accomplish this goal?
- A. Use cell-level encryption.
- B. Mask the data.
- C. Implement a DLP solution.
- D. Utilize encryption at rest.
Answer:
b
Question 9
A security analyst is monitoring an organization's IDS and DLP systems for an alert indicating files were removed from the network. The files were from the workstation of an employee who was authenticated but not authorized to access the files. Which of the following should the organization do FIRST to address this issue?
- A. Provide additional security awareness training.
- B. Disable the employee's credentials until the issue is resolved.
- C. Ask human resources to notify the employee that sensitive files were accessed.
- D. Isolate the employee's network segment and investigate further.
Answer:
d
Question 10
A security analyst is concerned that a malicious piece of code was downloaded on a Linux system. After some research, the analyst determines that the suspected piece of code is performing a lot of input/output (I/O) on the disk drive.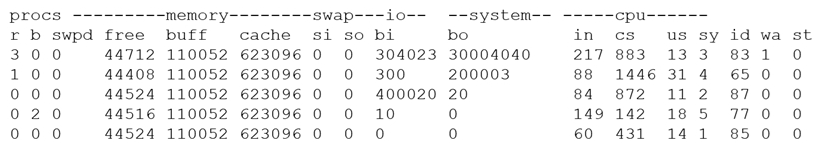
Based on the output above, from which of the following process IDs can the analyst begin an investigation?
- A. 65
- B. 77
- C. 83
- D. 87
Answer:
d